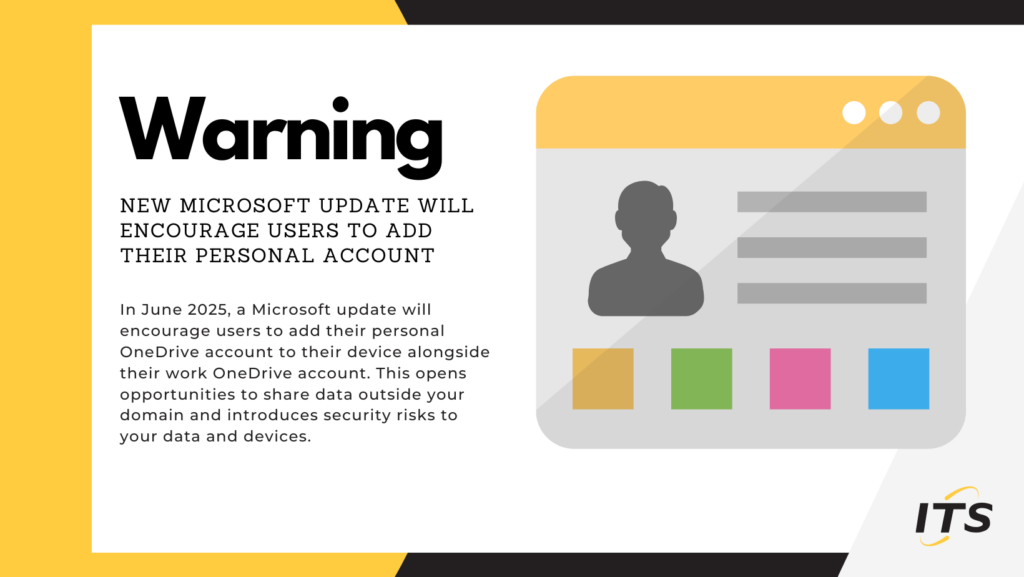
Microsoft will soon introduce a new feature to OneDrive that can impact data and device security for work accounts. The feature is called Prompt to Add Personal Account to OneDrive Sync. When a user logs in to their OneDrive account for work, Microsoft will prompt and encourage the user to also sync their personal OneDrive. […]
Featured
ITS Completes Annual SOC Audit
ITS is proud to announce the successful completion of our annual SOC audit – with an expanded scope that now includes our managed services processes and procedures under the SOC 2 framework. Our previous audits only covered our data center and related processes and services. This year, we added our managed services practice to the […]
New Ransomware Scam
The FBI periodically releases warnings and bulletins regarding popular scams that impact businesses and consumers. Their March 6 brief highlighted a scam rooted in cyberspace, but attacking victims through the postal service. Victims in this scheme are generally corporative executives. They receive a letter at their physical address warning them that their business has been […]
Cookie Choices
Understanding Cookies: What You Need to Know Have you ever visited a website and been greeted with a pop-up asking you to accept cookies? You’re not alone. But what exactly are cookies, and why should you care about how you handle them? What Are Cookies? Cookies are small text files that websites store on your […]
AI Office Pranks
One of our teammates recently took a well-deserved vacation—and found themselves on the receiving end of an AI-powered office prank. Leading up to their time off, the team had been discussing an office pizza party. So, naturally, we “planned” one while they were away. With just two quick photos of the office kitchen and a […]