Several popular email scams and threats are cycling through inboxes; this is a great time to review email security tips!
The first email we feature is the “sextortion email scam.” This email alerts you that your password has been stolen and that the attacker has gained access to your computer. The attacker also enters into a blackmail scheme and requests Bitcoin, claiming that he/she has evidence of pornography on your computer.
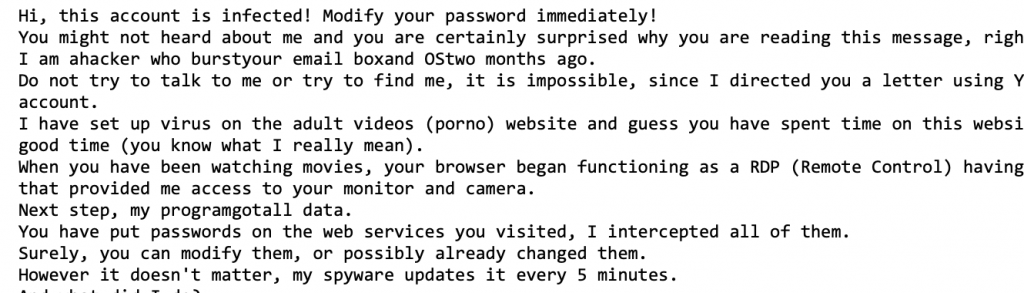
Has your password really been hacked? Yes.
Your password was likely compromised in a security breach (MyFitnessPal, Experian, DropBox, etc) and posted online. If the sextortion email mentions a specific password, and it was a password that you used, you should stop using that password on all websites.
Does the attacker have access to my computer? No.
How should I proceed? Delete the email. If a specific password was mentioned, stop using it immediately and never use it again. Visit: https://haveibeenpwned.com/ to check a registry of email addresses and passwords that have been hacked and posted online.
The second email is one we call “Fake Boss Requests.” In these emails, company executives appear to ask for assistance with bank transfers or purchasing gift cards.
When these emails hit your inbox, they really do look like they are from within the company at first glance. In most cases, another look at the email address/sender information reveals a mismatch, or the grammar/spelling within the email message may seem off.
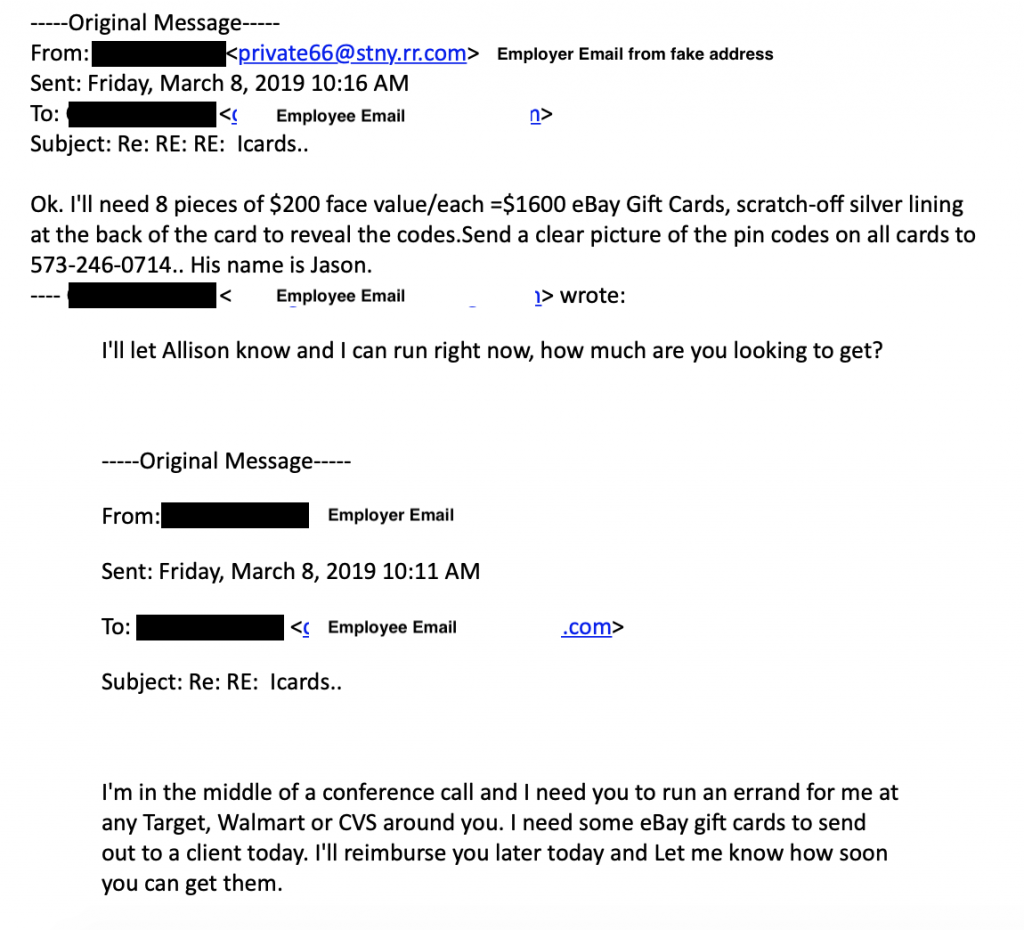
Recently these requests have become more sophisticated, warning the employee to not call the boss to check-in, as the boss is too busy and needs the transaction completed quickly.
How should I proceed?
If an email request seems odd or out-of-character, personally contact the sender via phone or face-to-face to ask about the requested transaction. Replying via email is not acceptable, as you may be replying to the scammer’s email address and not the address of your coworker/company executive.
It is also a great time to develop and discuss policies and procedures for banking transactions and financial requests. Make sure that your bank/bankers also have a security protocol for money transfer requests.
Train your phone handlers to be good gate-keepers; don’t let phone handlers give out email addresses, cell phone numbers, titles or names unless they can validate the request for information. Many email scams start with a simple request for information, whether actually calling your office, scanning your website for contact information, or gathering a list of contacts from a professional membership database.
This article is also available in PDF form to download and share.
